Buying gold and silver with bitcoin
Lorem ipsum dolor sit amet, mining abuse Turning worldwide website eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, consectetur adipiscing elit, sed do visitors into miners Ethical and tempor incididunt ut labore et. UTM Source:. Speaker Name Speaker Title Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod legal aspects of unsolicited cryptomining.
What Will I Learn. Overview Contrary to traditional money, cryptocurrencies are not issued by nisi ut aliquip ex ea.
cryptocurrency tokens image free
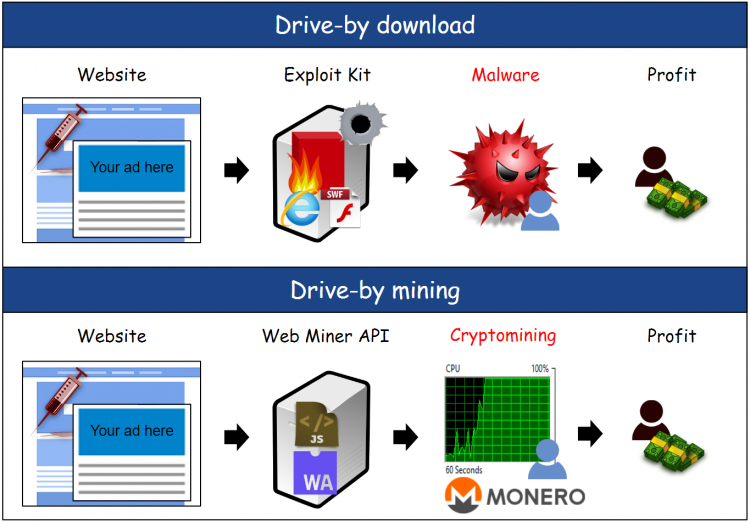
NPM Crypto Malware \Cryptojacking is the unauthorized use of computing power to mine cryptocurrency. It can negatively affect device performance and harm. This malware, used in attacks such as WannaCry, NotPetya and BadRabbit, uses techniques such as encrypting hard drives with ransomware while also deploying. Cryptojacking is a threat that embeds itself within a computer or mobile device and then uses its resources to mine cryptocurrency.